The Digital Operational Resilience Act (DORA) represents the European Union’s most ambitious attempt to harmonize rules on information and communication technology (ICT) risk management across financial entities. Designed to ensure that banks, insurers, investment firms, and critical third-party service providers can withstand, respond to, and recover from all types of ICT-related disruptions, DORA establishes uniform standards for governance, testing, incident reporting, and contractual requirements. This article explains:
- DORA’s legislative genesis and key objectives
- In-scope entities and phased compliance timelines
- Detailed ICT risk-management framework and governance mandates
- Advanced operational-resilience testing requirements
- Comprehensive incident-reporting procedures
- Strict oversight of third-party ICT providers
- Enforcement mechanisms and potential penalties
- Practical implementation strategies and challenges
- Interplay with existing EU regulations (e.g., NIS2, PSD2, GDPR)
- Future outlook for digital resilience in financial services
By the end of this article, risk officers, compliance specialists, and IT leaders will understand precisely how to embed DORA requirements into their operational processes and contractual relationships to achieve true digital resilience.
1. Legislative Background and Rationale
Digitalization has transformed financial services, driving efficiency but also concentration of ICT dependencies. Major outages—whether caused by software failures, cyberattacks, or cloud provider disruptions—have repeatedly demonstrated systemic vulnerabilities. High-profile incidents such as the SWIFT outage of 2021 and major cloud-provider service failures underscored the need for a uniform EU framework.
In response, the European Commission proposed DORA in September 2020 as part of its Digital Finance Strategy. After rigorous trilogue negotiations, the European Parliament and Council adopted DORA in November 2022. Member states must transpose the regulation into national law by January 17, 2025, with full compliance for financial firms by January 17, 2025, and for critical ICT third-party providers (CTPPs) by January 17, 2026.
Key Objectives
- Harmonize ICT risk management across financial entities to eliminate fragmented national approaches.
- Enhance digital operational resilience by mandating robust governance, testing, and incident-reporting regimes.
- Strengthen oversight of third-party ICT service providers ensuring they uphold the same resilience standards.
- Facilitate information sharing and coordinated responses to major ICT disruptions and cyber threats.
- Create clear enforcement pathways to deter non-compliance and incentivize continuous improvement.
2. Scope and Applicability
2.1 In-Scope Financial Entities
DORA applies directly to a wide range of financial institutions including:
- Credit institutions and payment service providers
- Investment firms and asset managers
- Insurance and reinsurance undertakings
- Trading venues, central counterparties (CCPs), and central securities depositories (CSDs)
- Crypto-asset service providers and crowdfunding platforms
- Financial market infrastructures (FMIs) and benchmark administrators
National competent authorities (NCAs) may extend certain requirements to smaller entities when systemic risk warrants.
2.2 Critical ICT Third-Party Providers (CTPPs)
A cornerstone of DORA is its binding oversight of ICT providers deemed “critical” based on the scale and systemic importance of their services. Major cloud-service providers, data analytics firms, and critical software vendors fall into this category. ESMA, EBA, and EIOPA maintain a list of designated CTPPs, subjecting them to direct supervisory powers under DORA from 2026 onward.
3. Governance and ICT Risk Management Framework
3.1 Board-Level Accountability
Board members of in-scope firms must assume ultimate responsibility for digital resilience. DORA mandates that governing bodies:
- Approve and periodically review ICT risk strategies
- Ensure sufficient resources and expertise for ICT risk management
- Integrate ICT resilience into overall risk appetite and business continuity planning
- Receive regular, comprehensive reports on ICT incidents, testing outcomes, and third-party performance
3.2 ICT Risk-Management Measures
Financial entities must implement a holistic set of measures to identify, protect, detect, respond to, and recover from ICT disruptions:
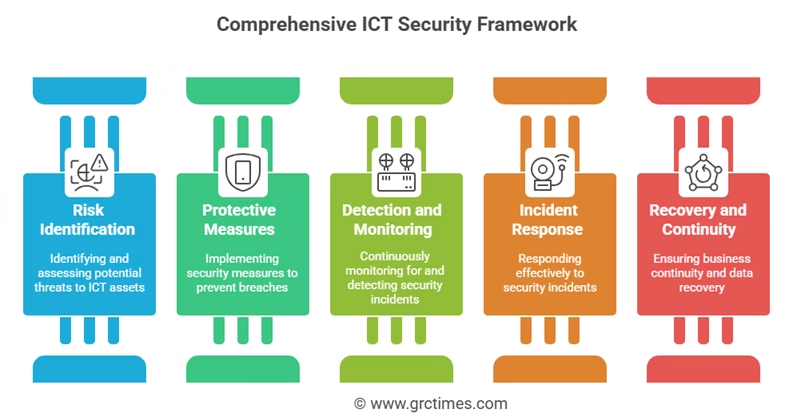
- Risk Identification
- Inventory of critical ICT assets, applications, and data flows
- Regular threat-landscape and vulnerability assessments
- Impact analyses mapping interdependencies
- Protective Measures
- Multi-factor authentication, encryption in transit and at rest
- Network segmentation and secure configuration management
- Secure software-development lifecycle (SDLC) for in-house applications
- Detection and Monitoring
- Continuous monitoring of network traffic and system logs
- Intrusion-detection and endpoint-detection platforms
- Threat-intelligence integration and anomaly detection
- Incident Response
- Formal incident-response plans with clear roles, escalation paths, and communication protocols
- Regular training and awareness programs for employees and third parties
- Recovery and Continuity
- Business continuity and disaster-recovery plans tested annually
- Data-backup solutions with defined recovery-time and recovery-point objectives
- Crisis-management exercises simulating major ICT outages
3.3 ICT Policy Documentation
Entities must produce and maintain up-to-date documentation of their ICT risk-management policies, procedures, and manuals. These documents must be readily available for review by NCAs and auditors.
4. Advanced Operational-Resilience Testing
4.1 Threat-Led Penetration Testing (TLPT)
DORA requires in-scope entities to conduct threat-led penetration tests at least once every three years or upon significant technological changes. Tests must be aligned with realistic threat scenarios, focusing on attacks that could disrupt critical services.
Key TLPT Requirements
- Engagement of qualified, independent testers
- Comprehensive scoping covering applications, infrastructure, and third-party interfaces
- Post-test reporting with prioritized remediation actions
- Board-level briefing on test outcomes and compliance status
4.2 Red-Team Exercises
Entities critical to financial market infrastructure must run annual red-team exercises simulating sophisticated, persistent attacks. Red teams assume the role of advanced adversaries, testing incident-detection, response, and recovery capabilities under stress.
4.3 Scenario-Based ICT Disruption Drills
All firms must plan and execute annual tabletop exercises simulating large-scale ICT outages—natural disasters, supply-chain failures, or regional power disruptions—to validate continuity plans and senior-management readiness.
5. Incident-Reporting and Information-Sharing Obligations
5.1 Classification of ICT Incidents
DORA mandates categorization of ICT incidents based on impact:
- Major Incident: Significant disruption to critical functions or data compromise affecting multiple entities or markets.
- Non-Major Incident: Localized or low-impact events requiring internal remediation without systemic consequences.
5.2 Reporting Timelines
- Initial Notification: Notify the relevant NCA or lead overseer (e.g., ESMA) within 24 hours of detecting a major incident.
- Detailed Report: Submit a comprehensive incident report—including root-cause analysis, impact assessment, and remediation measures—within one week.
- Follow-Up: Provide interim updates as requested by authorities until the incident is fully resolved.
Non-major incidents require semi-annual summary reports unless NCAs request individual notifications for specific cases.
5.3 Information-Sharing Schemes
DORA encourages voluntary sharing of incident indicators and threat intelligence within financial-sector information-sharing and analysis centers (FS-ISACs) and EU-CERT. Entities may request safe-harbor protections for voluntarily shared information.
6. Third-Party ICT Service-Provider Oversight
6.1 Contractual Requirements
All contracts with ICT providers—cloud services, data centers, software—must include mandatory clauses:
- Right to audit service providers’ ICT resilience measures
- Access to providers’ incident reports and test results
- Service-level agreements specifying recovery-time and recovery-point objectives
- Data-location and data-segregation provisions ensuring compliance with EU data-protection laws
- Exit-strategies and data-portability clauses to avoid vendor lock-in
6.2 Register of ICT Contracts
Firms must maintain a centralized register listing all material ICT contracts, renewal dates, critical service dependencies, and risk ratings. This register must be available to NCAs upon request.
6.3 Direct Oversight of CTPPs
Designated CTPPs face direct supervision by ESMA, EBA, or EIOPA, including:
- On-site inspections and off-site monitoring
- Mandates to report resilience-test outcomes and incidents
- Powers to impose binding mitigation measures and fines
7. Enforcement, Supervisory Cooperation, and Penalties
7.1 Supervisory Authorities
NCAs are responsible for supervising in-scope entities. The three ESAs (EBA, ESMA, EIOPA) coordinate to ensure consistent application of rules, share best practices, and issue joint guidance.
7.2 Penalties and Remediation
DORA authorizes NCAs to impose a range of measures for non-compliance:
- Remedial Orders: Directions to address specific ICT-resilience deficiencies within set deadlines.
- Periodic Penalty Payments: Daily fines for failure to comply with supervisory orders.
- Administrative Fines: Up to 1% of total annual turnover for breaches of ICT risk-management or incident-reporting requirements, and up to 2.5% for failures in third-party-provider oversight.
7.3 Cross-Border Cooperation
NCAs coordinate incident investigations and enforcement actions through the Joint Supervisory Framework, sharing information and issuing consistent supervisory messages to transnational entities.
8. Interplay with Existing EU Regulations
8.1 NIS2 Directive
DORA builds on NIS2’s broader cybersecurity requirements for critical infrastructure but adds financial-sector-specific obligations for resilience testing and third-party oversight. Entities in scope for both must align compliance efforts and reporting channels.
8.2 PSD2 and GDPR
- PSD2: DORA’s incident-reporting obligations complement PSD2’s requirement to report major payment-service incidents. Harmonized notification templates reduce duplication.
- GDPR: Data-breach notifications under GDPR may overlap with DORA reporting. Entities must determine which framework’s timeline applies and coordinate disclosures to NCAs and data-protection authorities.
9. Implementation Strategies
9.1 Conducting a Gap Analysis
- Map Current State: Inventory policies, controls, and incident-response procedures.
- Compare to DORA: Identify missing elements—governance, testing, contractual clauses.
- Prioritize Remediation: Focus first on high-risk ICT dependencies and critical-service contracts.
9.2 Embedding Resilience into Culture
- Executive Workshops: Engage boards and senior management in tabletop exercises.
- Staff Training: Integrate DORA requirements into regular cybersecurity training.
- Risk-Appetite Integration: Incorporate ICT-resilience metrics into enterprise-risk frameworks.
9.3 Third-Party-Provider Engagement
- Contract Review Campaign: Audit existing contracts against new mandatory clauses.
- Due Diligence Process: Enhance vendor-selection procedures with resilience criteria.
- Provider Scorecards: Track CTPP performance on resilience tests and incident histories.
9.4 Technology Investments
- Automated Monitoring: Deploy SIEM and XDR platforms for continuous threat detection.
- Testing Platforms: Engage specialized vendors for TLPT and red-team simulations.
- Resilience Dashboards: Develop real-time dashboards for board-level reporting on ICT health.
10. Key Challenges and Mitigation Techniques
- Resource Constraints: Small and mid-sized firms may lack budgets for extensive testing. Mitigate by pooling resources in sectoral ISACs and co-ordinating group exercises.
- Skill Gaps: Cyber-resilience expertise is scarce. Address through partnerships with academic institutions, professional associations, and external consultants.
- Regulatory Overlap: Managing dual reporting lines under DORA, NIS2, and PSD2 can be complex. Harmonize internal workflows and use unified reporting templates.
- Vendor Resistance: Major cloud providers may resist contractual changes. Leverage collective bargaining through industry associations and escalate unresolved issues to NCAs.
Frequently Asked Questions About DORA
What should a small credit union do if its core banking system goes offline due to a software bug?
The credit union must report a major ICT incident to its NCA within 24 hours of detection. It should provide an interim notification outlining affected services and estimated recovery time. Within one week, it must submit a detailed report including root-cause analysis, customer impact assessment, and remediation steps. Concurrently, it must activate its business-continuity plan to restore services and notify impacted customers as required by consumer-protection regulations.
If an insurer’s cloud-provider undergoes a regional outage, who is responsible for incident reporting?
Both the insurer and the designated CTPP (cloud provider) share reporting obligations. The insurer reports the disruption to its NCA per DORA timelines, while the cloud provider must notify ESMA or the relevant authority as a CTPP of a major incident. Contracts should ensure that the provider supplies all necessary technical details to the insurer for its report.
Can a fintech startup claim exemption if it serves fewer than 50,000 customers?
DORA does not offer exemptions based on customer count. Instead, applicability depends on entity type (e.g., payment institution, crypto-asset service provider). Startups must assess whether they fall within the regulation’s scope and, if so, comply fully regardless of size. NCAs may grant time-limited extensions, but no blanket exemptions exist.
What happens if a trading venue fails to conduct threat-led penetration tests every three years?
The trading venue faces potential supervisory orders requiring immediate testing and remediation. Continued non-compliance may trigger administrative fines up to 1% of total annual turnover. NCAs may also impose periodic penalty payments until the entity completes its TLPT and addresses critical findings.
How does DORA interact with GDPR when an ICT incident causes a data breach?
Entities must simultaneously fulfill DORA’s incident-reporting and GDPR’s personal-data-breach notification obligations. GDPR mandates reporting data breaches to data-protection authorities within 72 hours, while DORA requires a 24-hour major-incident notification. Firms should implement integrated workflows to satisfy both requirements without conflicting timelines.
If a CCP’s red-team exercise uncovers a systemic vulnerability, must the CCP report it as an incident?
Red-team findings alone do not constitute reportable incidents unless exploited in a real event. However, CCPs must document vulnerabilities, remediate promptly, and may share anonymized insights with supervisory authorities to demonstrate proactive risk management.
Are legacy IT systems exempt from DORA’s governance mandates?
No. All ICT assets—legacy or modern—fall under DORA’s governance framework. Entities must assess and secure outdated systems through compensating controls, replacement plans, or risk-mitigation measures. NCAs expect clear roadmaps for addressing legacy-technology risks.
How should a financial market infrastructure handle a cybersecurity threat detected in a third-party data-analytics vendor?
The infrastructure must escalate the issue per its incident-response plan and notify the vendor for immediate remediation. If the threat qualifies as a major incident, both parties must report to their respective supervisory authorities within 24 hours. Contracts should facilitate joint exercises and information exchange to resolve vulnerabilities swiftly.
