The Federal Risk and Authorization Management Program (FedRAMP) is the U.S. government’s standardized approach for assessing, authorizing, and continuously monitoring cloud services used by federal agencies. By adopting FedRAMP, agencies can leverage a “do once, use many times” framework that applies consistent security controls across cloud offerings, accelerating procurement while ensuring robust protection of sensitive data. For cloud service providers (CSPs), achieving FedRAMP authorization unlocks access to lucrative government contracts yet demands substantial documentation, technical rigor, and ongoing vigilance.
Table of Contents
FedRAMP Requirements
Authorization Paths
- Agency Authorization (ATO)
An individual federal agency sponsors the CSP, oversees the assessment by a Third-Party Assessment Organization (3PAO), and grants an agency-specific ATO. The CSP works directly with the sponsor to tailor controls to mission requirements. - Joint Authorization Board (JAB) P-ATO
The JAB—comprised of CIOs from GSA, DoD, and DHS—conducts a rigorous review of widely used cloud services, issuing a provisional P-ATO that participating agencies can reuse. JAB P-ATO is ideal for CSPs targeting multiple agencies. - FedRAMP Tailored
A streamlined baseline for low-impact, non-mission-critical SaaS solutions that handle only public or minimally sensitive Controlled Unclassified Information (CUI). Tailored reduces control requirements to core protections—access management, logging, encryption, and incident response—enabling faster authorization.
FedRAMP tailors the National Institute of Standards and Technology’s NIST SP 800-53 controls into three baselines—Low, Moderate, and High—based on data sensitivity and potential impact.
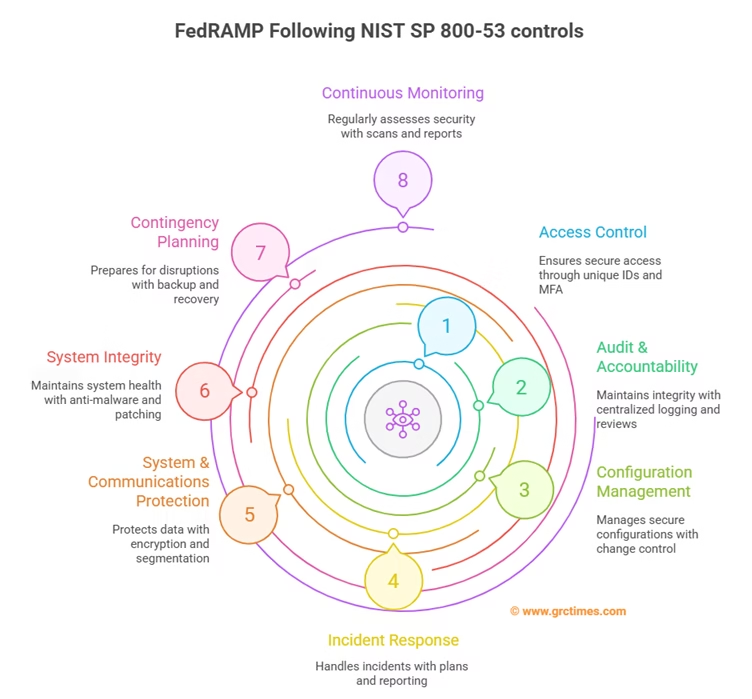
Each baseline comprises dozens of control families, including:
- Access Control (AC): unique user IDs, multi-factor authentication (MFA), least-privilege permissions, automated session time-outs.
- Audit & Accountability (AU): centralized logging of all user and system events, automated log review, integrity protection of log data.
- Configuration Management (CM): secure baseline configurations for hardware and software, documented change-control processes, continuous configuration monitoring.
- Incident Response (IR): formal incident response plan, cloud-specific playbooks, rapid agency/PMO reporting, post-incident reviews.
- System & Communications Protection (SC): encryption of data in transit (TLS 1.2+), data at rest (AES-256), network segmentation, boundary protection.
- System Integrity (SI): anti-malware defenses, automated patch management, runtime integrity monitoring, vulnerability scanning.
- Contingency Planning (CP): backup and restore processes, disaster recovery drills, documented Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs).
- Continuous Monitoring (CMO): weekly external vulnerability scans via an Approved Scanning Vendor (ASV), monthly control assessments, quarterly Security Status Reports, and annual penetration tests.
High-impact systems add further controls—for example, stricter personnel screening (background investigations) and enhanced physical security at data centers.
Impact on Stakeholders
- Cloud Service Providers must invest in documentation (System Security Plan, Security Assessment Plan, Plans of Action & Milestones), implement or enhance security controls, engage a FedRAMP-accredited Third-Party Assessment Organization (3PAO), and maintain continuous monitoring processes.
- Federal Agencies benefit from reusable authorizations, faster procurement, and a standardized assessment rubric, yet retain responsibility for tailoring requirements and overseeing CSP performance.
- End Users and Citizens gain increased assurance that government data in the cloud is safeguarded under rigorous, continuously enforced security measures, reducing the risk of breaches and service disruptions.
Best Practices for FedRAMP Success
- Establish a FedRAMP Governance Team comprising security architects, compliance managers, DevOps engineers, and legal advisors.
- Use Infrastructure as Code (IaC) tools (Terraform, ARM templates) to codify secure configurations, enforce drift detection, and simplify audits.
- Integrate security checks (static code analysis, dependency scanning, container vulnerability assessments) into CI/CD pipelines to catch issues early.
- Deploy a centralized Security Information and Event Management (SIEM) platform to correlate logs, automate alerting, and support forensic investigations.
- Maintain a well-practiced incident response program with regular table-top exercises and simulated cloud events.
- Engage the 3PAO early during readiness assessments to identify gaps and remediate controls before the formal evaluation.
- Automate evidence collection (control status, vulnerability scan results, patch records) using compliance management platforms to reduce manual overhead.
- Communicate proactively with sponsoring agencies or the Joint Authorization Board (JAB) PMO—flagging delays, discussing waiver requests, and sharing remediation progress.
Step-by-Step Compliance Process
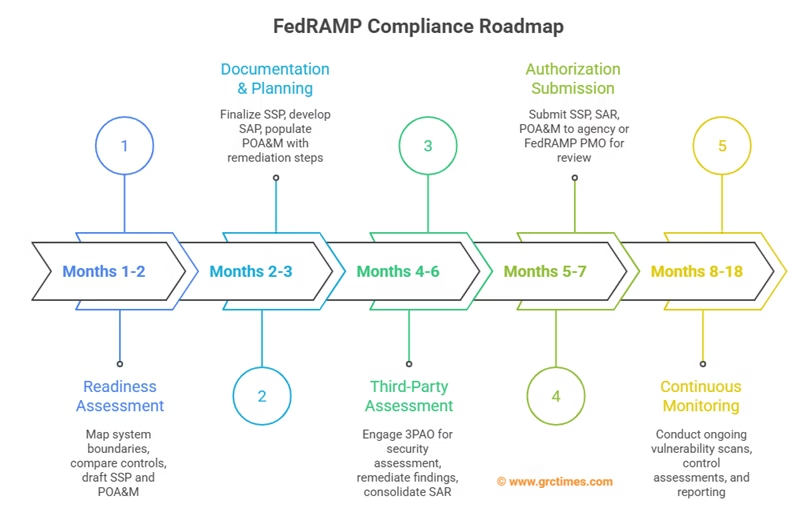
- Readiness Assessment
– Map system boundaries, data flows, and third-party dependencies.
– Compare current controls against the chosen FedRAMP baseline.
– Draft an initial System Security Plan (SSP) and a high-level Plan of Actions & Milestones (POA&M). - Documentation & Planning
– Finalize the SSP with detailed control implementation narratives.
– Develop the Security Assessment Plan (SAP) outlining 3PAO test procedures.
– Populate the POA&M with identified gaps and remediation steps, assigning owners and timelines. - Third-Party Assessment
– Engage an accredited 3PAO to perform the SAP-defined security assessment and penetration test.
– Review findings, remediate issues, update SSP and POA&M, and validate fixes.
– Consolidate the Security Assessment Report (SAR). - Authorization Submission
– Agency ATO: submit SSP, SAR, POA&M, policies, and procedures to the Authorizing Official.
– JAB P-ATO: submit package to FedRAMP PMO for JAB review; address feedback to receive provisional P-ATO.
– FedRAMP Tailored: submit streamlined package for low-impact SaaS approval. - Continuous Monitoring
– Conduct weekly external vulnerability scans (ASV) and remediate critical findings within 30 days.
– Perform monthly control assessments, updating the SSP and POA&M.
– Run annual penetration tests and validate high-impact controls.
– Submit quarterly Security Status Reports, including metrics on vulnerabilities, incidents, and POA&M progress.
– Prepare for triennial reauthorization by refreshing the SSP, SAR, and POA&M with current evidence.
Future Outlook
- Zero Trust Integration—FedRAMP will expand guidance on continuous authentication, least-privilege network segmentation, and policy-based access control across hybrid and multi-cloud environments.
- DevSecOps Evolution—automated security validation for serverless functions, container orchestration platforms (Kubernetes), and infrastructure as code, shaping real-time policy enforcement.
- Global Harmonization—alignment with European Union’s ENISA frameworks and the UK’s G-Cloud security requirements to streamline CSP offerings for allied governments.
- AI/ML Security Controls—emerging standards for model development pipelines, data integrity, algorithmic bias mitigation, and explainability in government AI/ML services.
- Supply Chain Risk Management—mandates for Software Bill of Materials (SBOMs), third-party component tracking, and enhanced vendor due diligence.
FedRAMP provides a robust, repeatable framework for securing cloud services across government, balancing rigorous security requirements with efficiency through reusable authorizations. By following best practices—strong governance, automation, continuous monitoring, and proactive stakeholder engagement—CSPs and agencies can successfully navigate the FedRAMP journey, ensuring reliable, trustworthy cloud solutions that safeguard federal data now and into the future.
Frequently Asked Questions
- Which FedRAMP baseline should I choose?
– Low for public or unclassified data, Moderate for Controlled Unclassified Information (CUI), High for national security–sensitive workloads. - How long does the FedRAMP process take?
– Plan for 9–15 months: 3–6 months readiness, 2–3 months 3PAO assessment, 3–6 months agency or JAB review. - What ongoing costs are involved?
– Annual monitoring: $50K–$150K (ASV scans, reporting tools), triennial reassessments: $100K–$300K. - Can one authorization serve multiple agencies?
– Yes—JAB P-ATOs are usable by any agency; agency ATOs often accepted through inter-agency agreements. - When is an unscheduled reassessment required?
– After critical incidents, major system changes, or significant FedRAMP baseline updates. - How does FedRAMP differ from CMMC?
– FedRAMP secures cloud services via NIST SP 800-53; CMMC governs DoD contractors using NIST SP 800-171 controls.
