The Payment Card Industry Data Security Standard (PCI DSS) stands as the cornerstone of payment security, protecting billions of credit card transactions worldwide. With over 2 billion payment card transactions occurring daily and credit card usage reaching nearly 80% of small businesses in the U.S., understanding PCI DSS compliance is not just a regulatory requirement, it’s a business imperative. This standard, established by the major credit card companies (Visa, Mastercard, American Express, Discover, and JCB) through the PCI Security Standards Council, sets the baseline for securing cardholder data across all organizations that store, process, or transmit payment card information.
Table of Contents
PCI DSS applies universally to all businesses that accept credit cards, regardless of transaction volume, geographical location, or processing method. From small retailers processing a few dozen transactions monthly to global enterprises handling millions of payments, every organization must comply with these security requirements. Non-compliance can result in devastating consequences: monthly fines ranging from $5,000 to $100,000, potential loss of payment processing privileges, and exposure to massive breach-related costs that can reach hundreds of millions of dollars.
Understanding PCI DSS Requirements
PCI DSS organizes its security framework around six fundamental control objectives, which expand into 12 specific requirements and over 300 sub-requirements. These controls work together to create a comprehensive security posture that protects cardholder data throughout its entire lifecycle.
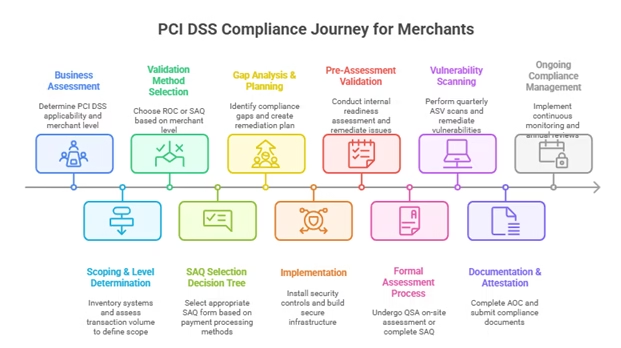
Build and Maintain a Secure Network and Systems: This foundational objective requires organizations to install and maintain firewall configurations that protect cardholder data from unauthorized access. Firewalls serve as the first line of defense, controlling traffic between trusted internal networks and untrusted external networks. Organizations must also eliminate vendor-supplied defaults for system passwords and security parameters, as these well-known configurations represent significant security vulnerabilities that attackers routinely exploit.
Protect Cardholder Data: Central to PCI DSS compliance is the protection of stored cardholder data through strong encryption methods and secure key management practices. Organizations must encrypt cardholder data both at rest and in transit, ensuring that even if data is intercepted or accessed by unauthorized parties, it remains unreadable without proper decryption keys. This includes implementing strong cryptography protocols like TLS 1.3 for data transmission and AES encryption for stored data.
Maintain a Vulnerability Management Program: This critical objective encompasses two key requirements. Organizations must protect all systems against malware by implementing and regularly updating anti-virus software, conducting periodic malware scans, and ensuring infected systems are promptly remediated. Additionally, businesses must develop and maintain secure systems and applications by applying security patches within one month of release for critical systems, conducting regular vulnerability assessments, and implementing secure coding practices.
Implement Strong Access Control Measures: Access controls form a crucial defense layer, requiring organizations to restrict access to cardholder data based on business need-to-know principles. Each individual with system access must have a unique user ID, enabling proper tracking and accountability. Organizations must also restrict physical access to cardholder data through appropriate security measures such as access controls, surveillance systems, and visitor management procedures.
Regularly Monitor and Test Networks: Continuous monitoring and testing ensure the ongoing effectiveness of security controls. Organizations must track and monitor all access to network resources and cardholder data, maintaining comprehensive logs for at least 12 months with three months immediately available for analysis. Regular testing of security systems and processes, including penetration testing and vulnerability scans, helps identify weaknesses before they can be exploited.
Maintain an Information Security Policy: The final objective requires organizations to establish, publish, maintain, and disseminate a comprehensive information security policy that addresses all PCI DSS requirements. This policy must be reviewed annually and updated whenever the environment changes, with all personnel receiving appropriate security awareness training to understand their responsibilities in protecting cardholder data.
PCI DSS Merchant Levels and Compliance Requirements
The PCI Security Standards Council classifies merchants into four levels based on their annual transaction volume, with each level carrying specific validation requirements that scale with the associated risk and business impact.
Level 1 merchants process over 6 million credit card transactions annually across all channels or have experienced a data breach that compromised account data. These high-volume merchants face the most stringent requirements, including an annual Report on Compliance (RoC) conducted by a Qualified Security Assessor (QSA), quarterly network vulnerability scans by an Approved Scanning Vendor (ASV), and completion of an Attestation of Compliance form. The comprehensive nature of Level 1 assessments reflects the significant risk these organizations pose to the payment ecosystem.
Level 2 merchants handle between 1 million and 6 million Visa or Mastercard transactions annually. While not requiring full QSA assessments, these organizations must complete an annual Self-Assessment Questionnaire (SAQ), conduct quarterly ASV scans, and submit an Attestation of Compliance. This level represents a balance between thorough security validation and operational practicality for medium-sized businesses.
Level 3 merchants process between 20,000 and 1 million e-commerce transactions annually. They follow the same validation requirements as Level 2 merchants—annual SAQ completion, quarterly vulnerability scanning, and attestation submission—but typically face less complex compliance scenarios due to their smaller scale of operations.
Level 4 merchants represent the largest group, including any business processing fewer than 20,000 e-commerce transactions annually or up to 1 million total transactions per year through any channel. While their requirements mirror those of Level 2 and 3 merchants, Level 4 organizations often qualify for simplified SAQ types that reduce the compliance burden while maintaining essential security protections.
The merchant level classification directly impacts the complexity and cost of compliance efforts. Level 1 merchants may spend hundreds of thousands of dollars annually on QSA assessments, remediation efforts, and ongoing security programs, while Level 4 merchants might achieve compliance for a few thousand dollars through appropriate SAQ completion and scanning services.
Self-Assessment Questionnaires (SAQs) and Their Types
Self-Assessment Questionnaires serve as the primary compliance validation tool for merchants at Levels 2, 3, and 4, offering a structured approach to documenting security measures and identifying compliance gaps. The PCI Security Standards Council has developed multiple SAQ types to accommodate different business models and processing environments, ranging from simple card-not-present scenarios to complex multi-channel operations.
SAQ A applies to card-not-present merchants who have completely outsourced all cardholder data functions to PCI DSS-validated third-party service providers. This streamlined questionnaire contains only 31 questions and represents the simplest compliance path for e-commerce businesses that never touch cardholder data directly. Eligibility requires absolute outsourcing—no electronic storage, processing, or transmission of cardholder data on the merchant’s systems.
SAQ A-EP addresses e-commerce merchants with websites that don’t receive cardholder data but could affect transaction security. These merchants partially outsource processing while maintaining some control over the payment environment. This SAQ includes additional requirements for website security, including the new PCI DSS 4.0 client-side protection requirements for payment page script integrity.
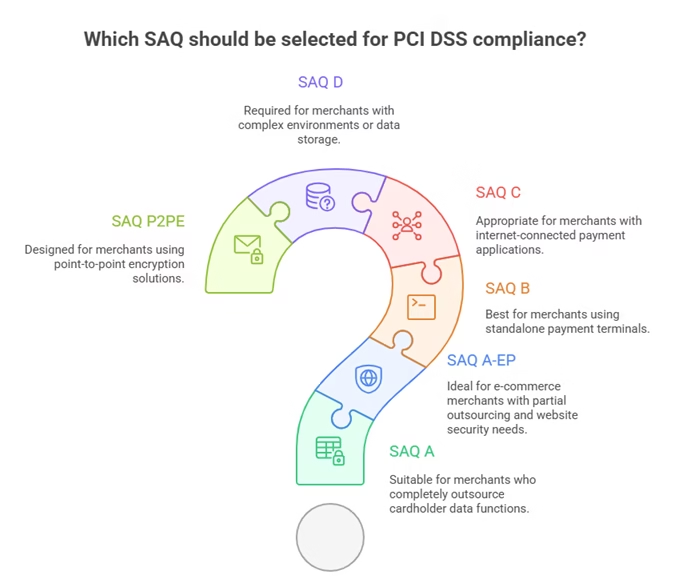
SAQ B covers merchants using dial-up terminals or point-of-sale systems that are not connected to other systems or networks. These standalone payment processing solutions represent a contained environment with limited connectivity, reducing the scope of compliance requirements while maintaining essential protections for the payment terminal itself.
SAQ C applies to merchants with payment application systems connected to the internet but without electronic storage of cardholder data. This category includes businesses using web-based payment applications or systems connected to networks, requiring more comprehensive security controls than isolated terminals.
SAQ D represents the most comprehensive self-assessment option, containing 251 questions for merchants (269 for service providers) and covering all PCI DSS requirements. Merchants who don’t qualify for other SAQ types must complete SAQ D, making it essential for businesses with complex processing environments or those storing cardholder data.
SAQ P2PE addresses merchants using validated Point-to-Point Encryption solutions, where cardholder data is encrypted at the point of capture and remains encrypted until it reaches the payment processor. This specialized SAQ recognizes the security benefits of end-to-end encryption while maintaining appropriate controls for the merchant environment.
The SAQ selection process requires careful analysis of the merchant’s specific processing environment, data flows, and storage practices. Choosing an incorrect SAQ type can lead to compliance gaps and potential penalties, making it essential to thoroughly understand the eligibility criteria for each questionnaire type.
The Financial Impact of Non-Compliance
PCI DSS violations carry severe financial consequences that extend far beyond simple regulatory fines, encompassing ongoing penalties, breach-related costs, business disruption, and reputational damage. Understanding the true cost of non-compliance helps organizations properly prioritize their security investments and compliance efforts.
Monthly Non-Compliance Fines represent the most immediate financial threat, starting at $5,000 to $10,000 per month for the first three months of non-compliance. These penalties escalate dramatically, reaching $25,000 to $50,000 monthly for months four through six, and can climb to $100,000 per month for extended non-compliance periods. Unlike one-time penalties, these fines continue accumulating until compliance is achieved, creating mounting financial pressure that can quickly become unsustainable for smaller businesses.
Data Breach Consequences represent the most catastrophic financial risk associated with non-compliance. When cardholder data is compromised, organizations face multiple layers of costs. Card networks charge up to $90 per impacted account, meaning a breach affecting one million accounts could result in $90 million in direct penalties alone. Additional breach-related expenses include forensic investigation costs, legal fees, customer notification expenses, credit monitoring services, and regulatory fines. Major breaches have resulted in settlements exceeding $400 million, as seen in cases like Equifax, demonstrating the potentially business-ending nature of these incidents.
Business Operations Impact extends beyond direct financial penalties to include loss of payment processing privileges, increased transaction fees, and enhanced scrutiny from acquiring banks. Organizations may face temporary or permanent suspension of their ability to accept credit cards, effectively shutting down payment-dependent businesses. Even when processing privileges are maintained, non-compliant merchants often face higher interchange rates and additional security requirements that increase operational costs.
Legal and Regulatory Consequences compound financial impacts through class-action lawsuits, state attorney general investigations, and regulatory enforcement actions. These proceedings can drag on for years, requiring substantial legal resources while exposing organizations to additional settlement costs and punitive damages. The legal costs alone often exceed the original compliance investment by orders of magnitude.
Small to medium-sized businesses face particularly severe consequences from PCI violations, as monthly fines of $5,000 to $100,000 can quickly exceed their available resources. Many organizations that experience significant breaches ultimately declare bankruptcy or cease operations entirely, highlighting the existential threat posed by non-compliance.
Best Practices for PCI DSS Compliance
Achieving and maintaining PCI DSS compliance requires a comprehensive approach that goes beyond basic requirement fulfillment to establish a robust security culture and operational framework. Organizations that treat compliance as an ongoing security improvement process rather than a annual checklist exercise demonstrate significantly better security outcomes and lower compliance costs over time.
Establish Comprehensive Governance through creation of a cross-functional PCI compliance team that includes representatives from information security, legal, operations, finance, and business leadership. This team should meet regularly to review compliance status, address emerging threats, assess policy updates, and ensure adequate resource allocation for security initiatives. Executive sponsorship is crucial for ensuring compliance efforts receive proper priority and funding throughout the organization.
Implement Risk-Based Security Controls by conducting thorough risk assessments that identify all systems, processes, and personnel that interact with cardholder data. Create detailed data flow diagrams that map how payment information enters, moves through, and exits your environment, identifying potential vulnerabilities at each stage. Use these assessments to implement appropriate security controls scaled to the risk level of each system component, ensuring that the most critical assets receive the strongest protection.
Deploy Advanced Technical Safeguards including network segmentation that isolates cardholder data environments from other business systems, reducing the scope of PCI compliance requirements while enhancing overall security. Implement multi-factor authentication for all access to cardholder data environments, ensuring that compromised credentials alone cannot lead to data exposure. Deploy comprehensive logging and monitoring solutions that provide real-time visibility into system activities and enable rapid detection of suspicious behavior.
Maintain Robust Vulnerability Management through regular security assessments, penetration testing, and vulnerability scanning that goes beyond minimum PCI requirements. Establish formal patch management processes that ensure critical security updates are tested and deployed within required timeframes while minimizing operational disruption. Implement continuous monitoring solutions that automatically identify new vulnerabilities and track remediation progress across the entire environment.
Invest in Employee Training and Awareness programs that go beyond annual compliance training to create ongoing security education. Develop role-specific training modules that address the unique risks and responsibilities associated with different job functions. Conduct regular phishing simulations and security awareness exercises that help employees recognize and respond appropriately to potential threats. Create clear incident reporting procedures that encourage prompt notification of potential security issues without fear of blame or punishment.
Engage Professional Compliance Support through relationships with Qualified Security Assessors, Approved Scanning Vendors, and specialized compliance consultants who can provide expert guidance throughout the compliance journey. These professionals bring deep expertise in PCI requirements interpretation, industry best practices, and emerging threats that can significantly improve compliance outcomes while reducing internal resource requirements.
Steps to Implement PCI DSS Compliance
Implementing PCI DSS compliance requires a systematic approach that ensures all requirements are properly addressed while minimizing business disruption and controlling costs. Organizations that follow a structured implementation methodology demonstrate higher success rates and lower long-term compliance costs compared to those that attempt ad hoc approaches.
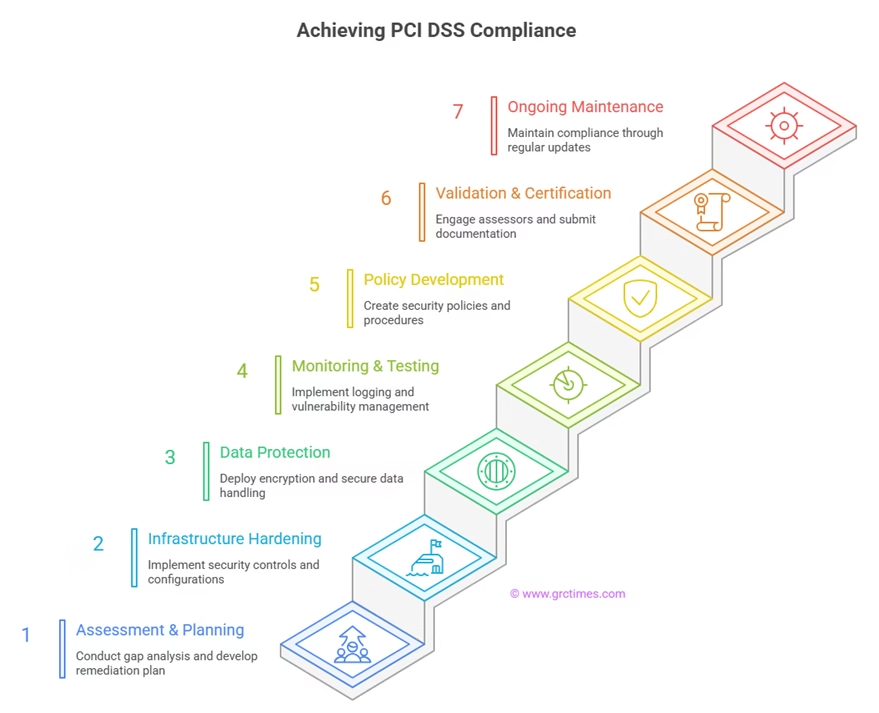
Phase 1: Assessment and Planning begins with conducting a comprehensive gap analysis that compares current security practices against PCI DSS requirements. Document all systems that store, process, or transmit cardholder data, including network devices, applications, databases, and third-party services. Create detailed network diagrams and data flow maps that identify all entry and exit points for payment information. Engage qualified security professionals to assess current controls and identify specific deficiencies that must be addressed. Develop a prioritized remediation plan that addresses the most critical gaps first while establishing realistic timelines and resource requirements for each phase of implementation.
Phase 2: Infrastructure Hardening focuses on implementing fundamental security controls including firewall configuration, network segmentation, access controls, and system hardening. Install and configure firewalls at all network boundaries, ensuring that only necessary traffic is permitted between network segments.
Implement network segmentation that isolates cardholder data environments from other business systems, reducing compliance scope and improving overall security. Change all default passwords and security settings on network devices, servers, and applications. Establish unique user accounts for all personnel requiring system access, implementing role-based access controls that limit privileges to the minimum necessary for job functions.
Phase 3: Data Protection Implementation involves deploying encryption solutions for both stored cardholder data and data in transit. Implement strong encryption algorithms (AES-256 for stored data, TLS 1.3 for transmission) with properly managed cryptographic keys. Establish secure key management processes that protect encryption keys throughout their lifecycle. Deploy data loss prevention solutions that monitor and control the movement of sensitive information. Implement secure deletion procedures that ensure cardholder data is properly removed when no longer needed for business purposes.
Phase 4: Monitoring and Testing Deployment requires implementation of comprehensive logging, monitoring, and vulnerability management capabilities. Deploy centralized log management solutions that collect, correlate, and analyze security events from all system components.
Implement real-time monitoring that can detect and alert on suspicious activities or potential security incidents. Establish vulnerability scanning procedures that identify security weaknesses before they can be exploited. Deploy anti-malware solutions on all systems susceptible to malicious software, ensuring regular updates and comprehensive scanning.
Phase 5: Policy and Procedure Development encompasses creation of comprehensive information security policies that address all PCI DSS requirements. Develop detailed procedures for incident response, access management, change control, and vendor management. Create user awareness training programs that educate personnel about their security responsibilities. Establish formal risk management processes that guide security decision-making throughout the organization.
Phase 6: Validation and Certification involves engaging appropriate validation resources based on merchant level requirements. Level 1 merchants must work with Qualified Security Assessors to conduct comprehensive on-site assessments and produce formal Reports on Compliance. Merchants at other levels complete appropriate Self-Assessment Questionnaires with supporting evidence.
All merchants must engage Approved Scanning Vendors to conduct quarterly vulnerability scans of external-facing systems. Submit completed compliance documentation to acquiring banks and maintain evidence files for annual review cycles.
Phase 7: Ongoing Maintenance establishes processes for maintaining compliance over time through regular monitoring, testing, and updates. Conduct quarterly internal assessments to ensure controls remain effective and appropriate. Review and update policies and procedures annually or when significant changes occur in the business environment. Maintain current relationships with compliance professionals who can provide guidance on evolving requirements and emerging threats.
PCI DSS 4.0 and Future Developments
PCI DSS 4.0 represents the most significant update to the standard in over a decade, introducing new requirements that address evolving threats in the digital payment landscape. The transition period concluded on March 31, 2025, making full compliance with version 4.0 mandatory for all organizations. Understanding these changes is crucial for maintaining effective security programs and avoiding compliance gaps that could expose organizations to penalties and increased breach risk.
Multi-Factor Authentication Requirements now mandate MFA for all access into cardholder data environments, elevating what was previously a best practice to a mandatory control. This requirement applies to administrative access, user accounts with access to cardholder data, and any system that can affect the security of the cardholder data environment.
Organizations must implement MFA solutions that provide strong authentication using something you know (passwords), something you have (tokens), and something you are (biometrics). The implementation of comprehensive MFA represents one of the most challenging technical requirements in PCI DSS 4.0, often requiring significant infrastructure investments and workflow modifications.
Client-Side Security Controls address the growing threat of attacks targeting payment pages and e-commerce websites. Requirements 6.4.3 and 11.6.1 mandate implementation of script inventory systems that track all JavaScript and other executable code on payment pages, along with monitoring for unauthorized modifications.
Organizations must implement Content Security Policy (CSP), Subresource Integrity (SRI), and real-time monitoring solutions that detect tampering with payment processing scripts. These requirements respond to the increasing prevalence of client-side attacks that inject malicious code into payment pages to steal cardholder data.
Enhanced Vulnerability Management introduces more sophisticated approaches to identifying, assessing, and remediating security vulnerabilities. Organizations must implement risk-based vulnerability management programs that consider business impact, exploit availability, and environmental factors when prioritizing remediation efforts. The updated requirements emphasize continuous monitoring and assessment rather than periodic point-in-time evaluations, reflecting the dynamic nature of modern threat landscapes.
Customized Approach Options provide organizations with flexibility to implement alternative controls that achieve equivalent security outcomes to traditional requirements. This new framework allows businesses to propose innovative security solutions that may be more appropriate for their specific environments while maintaining the overall security objectives of PCI DSS. However, the customized approach requires extensive documentation, risk assessment, and validation by qualified security professionals, making it suitable primarily for large organizations with sophisticated security programs.
Looking ahead, future PCI DSS developments will likely focus on emerging technologies including artificial intelligence, machine learning, cloud-native architectures, and mobile payment solutions. The standard will continue evolving to address new attack vectors such as supply chain compromises, nation-state threats, and advanced persistent threats that specifically target payment infrastructure. Organizations should expect continued emphasis on zero-trust architectures, automated threat detection and response, and integration with broader cybersecurity frameworks.
Global Harmonization efforts will increasingly align PCI DSS with international standards such as ISO 27001, NIST Cybersecurity Framework, and regional regulations like GDPR. This convergence will help organizations streamline compliance efforts across multiple frameworks while maintaining consistent security outcomes. The payment industry will likely see increased cooperation between PCI DSS and emerging Central Bank Digital Currency (CBDC) standards as digital payment methods continue expanding globally.
Figure 2: Merchant Level Requirements Matrix – A detailed comparison table showing the specific validation requirements for each merchant level, including SAQ types, QSA requirements, ASV scanning obligations, and attestation procedures. This matrix would help organizations quickly understand their compliance obligations based on transaction volume and processing methods.
PCI DSS compliance represents far more than a regulatory checkbox—it serves as the foundation for protecting customer trust, business continuity, and financial stability in our increasingly digital economy. Organizations that embrace PCI DSS as a comprehensive security framework rather than a compliance burden consistently demonstrate better security outcomes, lower breach risks, and reduced long-term costs.
The evolution to PCI DSS 4.0 reflects the payment industry’s commitment to staying ahead of emerging threats while providing practical frameworks that businesses of all sizes can implement effectively. As payment technologies continue advancing and threat landscapes evolve, PCI DSS will remain the critical standard ensuring that cardholder data receives appropriate protection across the global payment ecosystem. Success in PCI compliance requires ongoing commitment, adequate resources, and a security-first mindset that prioritizes customer protection above all other considerations.
Frequently Asked Questions
1. What types of businesses must comply with PCI DSS?
Any organization that stores, processes, transmits, or could impact the security of cardholder data must comply with PCI DSS. This includes merchants of all sizes, payment processors, service providers, and any third-party vendors that have access to cardholder data environments. Even businesses that process only a few credit card transactions annually must maintain compliance.
2. How often must PCI DSS compliance be validated?
Compliance validation frequency depends on merchant level. Level 1 merchants require annual QSA assessments and quarterly vulnerability scans. Merchants at Levels 2, 3, and 4 must complete annual SAQs and quarterly ASV scans. Additionally, compliance must be revalidated whenever significant changes occur in the processing environment.
3. What is the difference between PCI compliance and PCI certification?
PCI DSS compliance refers to meeting all security requirements outlined in the standard, while certification specifically relates to the formal validation process conducted by approved assessors. Merchants demonstrate compliance through SAQs or QSA assessments, but only QSAs can issue formal certification reports. The terms are often used interchangeably, though technically compliance is the security state and certification is the validation process.
4. Can cloud services help with PCI compliance?
Cloud services can significantly simplify PCI compliance by reducing the scope of merchant responsibilities, particularly when using validated cloud providers that maintain their own PCI compliance. However, merchants remain ultimately responsible for ensuring their cloud configurations and processes meet PCI requirements. Shared responsibility models require careful understanding of which security controls are managed by the cloud provider versus the merchant.
5. What happens if a PCI-compliant organization experiences a data breach?
PCI compliance does not prevent all possible data breaches, but it significantly reduces risk and can limit liability in the event of an incident. Compliant organizations may face reduced fines, lower remediation costs, and less regulatory scrutiny following a breach. However, they must still conduct forensic investigations, notify affected parties, and may face some penalties depending on the circumstances of the incident.
6. How much does PCI DSS compliance typically cost?
Compliance costs vary dramatically based on merchant level, processing environment complexity, and current security posture. Level 4 merchants might spend $2,000-$10,000 annually on basic compliance requirements, while Level 1 merchants often invest $100,000-$500,000 or more in comprehensive programs including QSA assessments, remediation efforts, and ongoing security measures.
7. What is tokenization and how does it affect PCI scope?
Tokenization replaces sensitive cardholder data with non-sensitive tokens that have no intrinsic value if compromised. Properly implemented tokenization can significantly reduce PCI DSS scope by eliminating cardholder data from merchant environments. However, the tokenization system itself must be properly secured and validated, and merchants must ensure they’re not inadvertently storing original cardholder data alongside tokens.
8. How do I choose the right SAQ for my business?
SAQ selection depends on how your business processes cardholder data, what systems are involved, and whether you store payment information. Start by reviewing the eligibility criteria for each SAQ type, create detailed data flow diagrams of your payment processes, and consult with your acquiring bank or a qualified security professional if you’re uncertain. Choosing the wrong SAQ can lead to compliance gaps and potential penalties.
9. What should I do if I discover I’m not currently PCI compliant?
Begin by conducting a comprehensive gap analysis to identify all compliance deficiencies, then develop a prioritized remediation plan that addresses the most critical vulnerabilities first. Engage qualified security professionals to help develop and implement corrective measures. Communicate with your acquiring bank about your situation and compliance timeline, as early disclosure often results in more favorable treatment than discovered violations.
10. How does PCI DSS 4.0 differ from previous versions?
PCI DSS 4.0 introduces significant new requirements including mandatory multi-factor authentication, client-side security controls for payment pages, enhanced vulnerability management, and customized approach options. The deadline for full 4.0 compliance was March 31, 2025, meaning all organizations must now meet these updated requirements. The changes reflect evolving threats in the digital payment landscape and emphasize continuous monitoring over periodic assessments.
