The intersection of e-discovery and compliance presents organizations with a complex landscape where vast volumes of data, evolving regulations, and the need for rapid, defensible processes collide. As regulatory bodies increase scrutiny and the types of data under review become ever more nuanced, leveraging specialized compliance GRC software has become a strategic imperative for modern legal operations.
The Critical Challenge Landscape
Data Volume and Complexity: The Digital Deluge
Organizations today generate unprecedented volumes of structured and unstructured data across emails, instant messaging platforms, collaborative workspaces, cloud storage systems, and third-party applications. The eDiscovery market is projected to surge past $25 billion by 2029, driven primarily by this exponential growth in digital evidence.
Modern legal teams face the daunting task of processing not just traditional documents, but also dynamic data types including chat logs, social media communications, mobile device data, and ephemeral messaging platforms that present unique preservation challenges. The complexity is further amplified by the need to maintain native file formats while ensuring metadata integrity throughout the discovery lifecycle.
Regulatory Complexity: Navigating Multiple Jurisdictions
The regulatory environment has become increasingly complex with overlapping requirements from multiple jurisdictions and industry-specific mandates. Organizations must comply with federal rules such as the Federal Rules of Civil Procedure (FRCP), state-specific requirements, and international regulations like GDPR when dealing with cross-border data.
Data privacy protection legislation adds another layer of complexity, particularly when dealing with personal information across different jurisdictions with varying data subject rights and processing restrictions. The rise of new privacy regulations continues to introduce additional compliance obligations that must be integrated into existing e-discovery frameworks.
Timing Pressures and Defensibility Requirements
Courts and regulators impose strict deadlines for data collection, review, and production, creating intense pressure on legal teams to respond quickly while maintaining defensibility. The “reasonable anticipation of litigation” standard creates ambiguity about when preservation obligations begin, requiring organizations to develop proactive triggers and response protocols.
Maintaining an unbroken chain of custody has become increasingly critical as digital evidence faces greater scrutiny regarding authenticity and integrity. Any gaps in documentation or handling procedures can result in evidence being deemed inadmissible, potentially undermining entire cases.
Cost Control and Resource Optimization
Manual review processes and ad hoc workflows can rapidly escalate legal costs, particularly as data volumes continue to grow. Organizations face pressure to deliver faster results without expanding budgets, forcing a fundamental rethinking of resource allocation and process efficiency.
The challenge is compounded by the need for specialized technical expertise to handle complex data formats, implement proper preservation techniques, and manage sophisticated e-discovery technologies.
How Compliance GRC Software Addresses These Challenges
- Centralized Data Repository and Governance
- Modern compliance GRC platforms aggregate data from disparate sources into unified, secure environments that provide comprehensive visibility across the entire data ecosystem. These systems implement automated data classification and tagging capabilities that facilitate rapid identification and retrieval of relevant information during discovery processes.
- Advanced platforms offer API-based integration with enterprise systems, enabling seamless data collection from various sources while maintaining proper access controls and security measures. This centralization eliminates data silos and reduces the time required to locate and preserve relevant information across complex IT infrastructures.
- Automated Workflows and Process Standardization
- Compliance GRC software implements pre-defined playbooks for legal holds, custodian notifications, review assignments, and escalation procedures. These automated workflows minimize manual errors and accelerate response times while ensuring consistent application of policies and procedures.
- Legal hold automation features enable organizations to quickly identify relevant custodians, deploy hold notifications, track acknowledgments, and monitor compliance across hundreds or thousands of employees. Automated reminder systems and escalation protocols ensure that preservation obligations are maintained throughout the litigation lifecycle.
- Advanced Search and Analytics Capabilities
- Modern platforms leverage artificial intelligence and machine learning algorithms to enhance search capabilities beyond traditional keyword approaches. These systems employ concept-based searching, predictive coding, and technology-assisted review (TAR) to identify relevant documents more efficiently and accurately.
- AI-powered analytics help prioritize high-risk documents for review, identify patterns and relationships within data sets, and provide early case assessment capabilities that inform litigation strategy. These technologies significantly reduce the volume of documents requiring human review while improving the quality of document identification.
- Policy Management and Compliance Enforcement
- GRC platforms enforce retention and deletion policies automatically, reducing data sprawl and ensuring only relevant information is preserved for potential discovery. These systems provide centralized policy management capabilities that can be updated and deployed across the organization as regulatory requirements evolve.
- Automated compliance monitoring tracks adherence to legal holds, retention schedules, and data handling procedures, providing real-time visibility into compliance status and flagging potential violations before they become critical issues.
- Comprehensive Audit and Reporting Capabilities
- Robust audit trail functionality captures detailed logs of all system interactions, including user access, document modifications, search activities, and data exports. These comprehensive records provide the documentation necessary to demonstrate compliance and maintain defensible processes.
- Automated reporting capabilities generate regulatory compliance reports, legal hold status updates, and discovery metrics that support both internal governance and external regulatory requirements. These reports provide stakeholders with real-time visibility into discovery progress and compliance status.
Detailed Implementation Framework
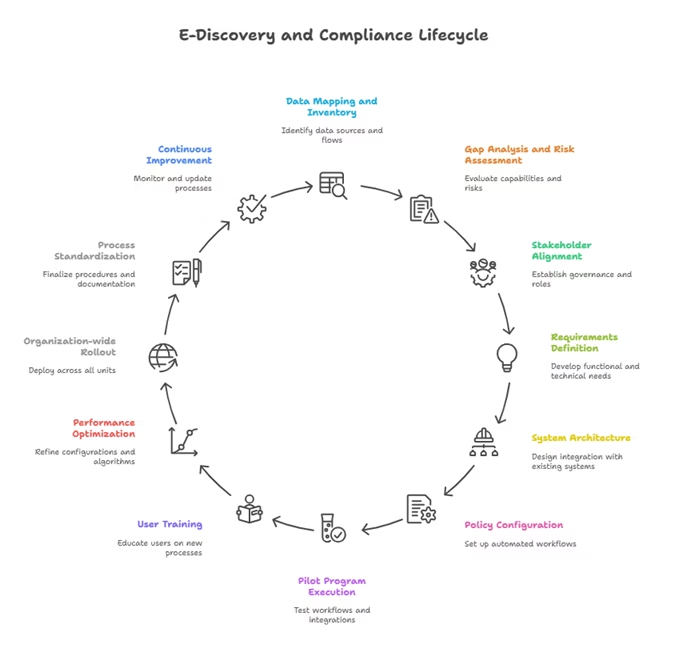
Phase 1: Assessment and Planning (Months 1-2)
Data Mapping and Inventory
- Conduct comprehensive data mapping exercises to identify all sources of potentially discoverable information across the organization
- Create detailed data flow diagrams showing how information moves between systems, applications, and storage repositories
- Document data ownership, custodianship, and access controls for each identified data source
- Assess current data retention and disposal practices against legal and regulatory requirements
Gap Analysis and Risk Assessment
- Compare current e-discovery and compliance capabilities against industry best practices and regulatory requirements
- Identify gaps in preservation capabilities, workflow automation, and reporting functionality
- Assess current vendor relationships and evaluate consolidation opportunities
- Document potential risk exposures and compliance vulnerabilities
Stakeholder Alignment and Governance Structure
- Establish cross-functional project teams including legal, IT, compliance, and business stakeholders
- Define roles, responsibilities, and decision-making authority for the implementation process
- Create project governance structures with regular reporting and escalation procedures
- Develop change management strategies to ensure user adoption and process compliance
Phase 2: Platform Selection and Configuration (Months 2-4)
Requirements Definition and Vendor Evaluation
- Develop detailed functional and technical requirements based on gap analysis findings
- Evaluate multiple GRC platforms against defined criteria including scalability, integration capabilities, and security features
- Conduct proof-of-concept testing with shortlisted vendors using representative data sets
- Negotiate contracts that include appropriate service level agreements and data security provisions
System Architecture and Integration Planning
- Design system architecture that integrates with existing IT infrastructure and security frameworks
- Plan API integrations with key business systems including email, collaboration platforms, and document management systems
- Develop data migration strategies for existing archives and preserved data sets
- Create security configurations that meet organizational and regulatory requirements
Policy and Workflow Configuration
- Configure automated workflows for legal holds, custodian notifications, and review processes
- Implement data retention and disposal policies within the platform
- Create user role definitions and access controls based on organizational structure and security requirements
- Develop standard operating procedures for common e-discovery and compliance scenarios
Phase 3: Pilot Implementation and Testing (Months 4-6)
Pilot Program Design and Execution
- Select representative use cases for pilot implementation including different case types and data volumes
- Execute end-to-end workflows from legal hold issuance through document production
- Test integration points with existing systems and validate data accuracy and completeness
- Document lessons learned and identify areas requiring additional configuration or training
User Training and Change Management
- Develop role-based training programs for different user groups including legal staff, IT personnel, and business custodians
- Create user documentation and quick reference guides for common tasks and procedures
- Implement change management initiatives to encourage adoption and address resistance
- Establish user feedback mechanisms to continuously improve processes and procedures
Performance Optimization and Fine-tuning
- Monitor system performance and optimize configurations based on actual usage patterns
- Refine search algorithms and analytical models based on pilot results
- Adjust workflow parameters to improve efficiency and user experience
- Validate audit trail functionality and reporting accuracy
Phase 4: Full Deployment and Scaling (Months 6-9)
Organization-wide Rollout
- Deploy the platform across all relevant business units and geographic locations
- Migrate existing legal holds and preserved data sets to the new system
- Implement comprehensive monitoring and alerting capabilities
- Execute communication plans to inform all stakeholders of new procedures and capabilities
Process Standardization and Documentation
- Finalize standard operating procedures for all e-discovery and compliance workflows
- Create comprehensive documentation for system administration and user support
- Implement quality assurance processes to ensure consistent application of policies and procedures
- Establish performance metrics and key performance indicators (KPIs) for ongoing monitoring
Integration and Optimization
- Complete remaining system integrations with third-party applications and services
- Optimize workflow performance based on actual usage data and user feedback
- Implement advanced analytics and reporting capabilities
- Establish ongoing support and maintenance procedures
Phase 5: Continuous Improvement and Maturity (Ongoing)
Performance Monitoring and Optimization
- Establish regular review cycles for system performance, user satisfaction, and compliance effectiveness
- Monitor key metrics including response times, cost per case, and compliance rates
- Conduct regular audits of processes and procedures to identify improvement opportunities
- Update configurations and workflows based on changing business needs and regulatory requirements
Technology Evolution and Enhancement
- Stay current with platform updates and new feature releases from vendors
- Evaluate emerging technologies such as advanced AI capabilities and new data source integrations
- Plan for scalability as data volumes and case complexity continue to grow
- Assess opportunities for additional automation and workflow optimization
Regulatory Adaptation and Compliance
- Monitor evolving regulatory requirements and update policies and procedures accordingly
- Participate in industry forums and working groups to stay informed of best practices
- Conduct regular compliance assessments and remediation activities
- Update training programs and documentation to reflect new requirements and procedures
Industry Best Practices for Implementation Success
Data Governance and Information Management
- Comprehensive Data Mapping
Organizations must maintain detailed inventories of all data sources, including location, format, retention requirements, and business purpose. This mapping should be updated regularly to reflect changes in technology, business processes, and organizational structure. - Automated Classification and Retention
Implement automated data classification systems that apply consistent retention and disposal schedules based on business value and legal requirements. This reduces overall data volumes while ensuring that potentially relevant information is appropriately preserved. - Data Quality and Integrity Management
Establish data quality standards and monitoring processes that ensure the accuracy, completeness, and integrity of preserved information. This includes implementing checksums, version controls, and other technical measures to detect unauthorized modifications.
Legal Hold Management Excellence
- Proactive Trigger Identification
Develop clear criteria for when legal hold obligations are triggered, erring on the side of caution rather than waiting for formal litigation to commence. Create standardized assessment procedures that can be consistently applied across different types of potential disputes. - Comprehensive Custodian Management
Implement systematic approaches to custodian identification that leverage HR systems and organizational data to ensure complete coverage. Maintain current contact information and employment status to facilitate rapid hold deployment when needed. - Continuous Monitoring and Compliance
Establish ongoing monitoring procedures that track custodian compliance with legal hold obligations. Implement escalation procedures for non-responsive custodians and maintain detailed documentation of all hold management activities.
Technology Integration and Automation
- API-First Integration Strategy
Prioritize platforms that offer robust API capabilities for integration with existing business systems. This ensures that data can be collected and preserved without requiring manual intervention or system disruptions. - Workflow Automation and Standardization
Implement standardized workflows for common e-discovery tasks including legal holds, collection, processing, and review. These workflows should include appropriate approval processes, quality controls, and documentation requirements. - Advanced Analytics and AI Integration
Leverage artificial intelligence and machine learning capabilities to improve the efficiency and accuracy of document review and analysis. These technologies should be implemented with appropriate human oversight and quality control measures.
Security and Risk Management
- End-to-End Security Framework
Implement comprehensive security measures that protect sensitive information throughout the entire e-discovery lifecycle. This includes encryption of data in transit and at rest, access controls, and secure processing environments. - Chain of Custody and Audit Trails
Maintain detailed documentation of all activities related to data collection, processing, and production. These audit trails must demonstrate the integrity and authenticity of preserved information and support defensibility arguments. - Incident Response and Continuity Planning
Develop comprehensive incident response procedures for security breaches, system failures, and other disruptions that could impact e-discovery obligations. Include backup and recovery procedures that ensure business continuity and preservation compliance.
Measuring Success and ROI
Quantitative Metrics
Operational Efficiency Indicators
- Reduction in time from legal hold issuance to custodian acknowledgment
- Decrease in manual processing time for data collection and review
- Improvement in document review throughput and accuracy rates
- Reduction in overall discovery costs per case or per gigabyte processed
Compliance and Risk Metrics
- Decrease in preservation failures and spoliation incidents
- Improvement in regulatory audit results and compliance ratings
- Reduction in discovery-related sanctions and adverse rulings
- Enhancement in overall legal risk management effectiveness
Qualitative Benefits
Strategic Value Creation
- Enhanced ability to make informed litigation decisions based on early case assessment
- Improved client satisfaction through faster response times and better communication
- Increased competitive advantage through superior legal technology capabilities
- Better alignment between legal, compliance, and business objectives
Organizational Capability Building
- Development of specialized expertise in legal technology and data management
- Creation of standardized processes that support organizational scaling
- Enhancement of overall information governance maturity
- Improvement in cross-functional collaboration and communication
Future Trends and Considerations
Emerging Technology Integration
- Artificial Intelligence and Machine Learning
The continued evolution of AI capabilities will enable more sophisticated document analysis, predictive coding, and automated decision-making in e-discovery processes. Organizations should prepare for these advances by building flexible platforms that can incorporate new AI tools and techniques. - Cloud-Native Architectures
The shift toward cloud-native e-discovery platforms will provide greater scalability, flexibility, and cost-effectiveness. Organizations should evaluate their cloud strategies and ensure that chosen platforms can operate effectively in hybrid and multi-cloud environments.
Regulatory Evolution
- Privacy and Data Protection
Continuing evolution of privacy regulations worldwide will require ongoing adaptation of e-discovery processes to balance transparency obligations with privacy protection requirements. Organizations must build flexibility into their systems to accommodate changing regulatory landscapes. - Cross-Border Compliance Complexity
As organizations become increasingly global, the complexity of managing e-discovery across multiple jurisdictions will continue to grow. Platforms must provide capabilities to manage jurisdiction-specific requirements while maintaining operational efficiency.
Frequently Asked Questions (FAQ)
Q1: What is the primary difference between traditional e-discovery and compliance-integrated approaches?
Traditional e-discovery often operates as a reactive, case-specific process focused solely on litigation response. Compliance-integrated approaches proactively manage data governance, retention, and preservation as part of ongoing business operations, making discovery more efficient and defensible when legal matters arise. This integration reduces costs, improves response times, and ensures better compliance with regulatory requirements.
Q2: How does automated workflow technology improve legal hold management?
Automated workflows eliminate manual processes that are prone to errors and delays. They provide standardized custodian identification, automatic notification deployment, tracking of acknowledgments, and escalation procedures for non-compliance. This automation reduces the average time to deploy legal holds from days to hours while providing comprehensive audit trails that demonstrate compliance efforts.
Q3: What are the key security considerations when implementing GRC software for e-discovery?
Security considerations include end-to-end encryption for data in transit and at rest, role-based access controls, comprehensive audit logging, and secure processing environments. Organizations must also ensure compliance with attorney-client privilege requirements, maintain proper chain of custody documentation, and implement appropriate data residency controls for cross-border matters.
Q4: How can organizations measure the ROI of e-discovery and compliance automation?
ROI can be measured through multiple metrics including reduced processing time, lower per-case costs, decreased external counsel expenses, and improved compliance ratings. Organizations typically see 35% improvements in workflow efficiency and 25% reductions in missed deadlines. Additional value comes from reduced legal risks, faster case resolution, and enhanced ability to make strategic litigation decisions based on early case assessment capabilities.
Q5: What challenges should organizations expect when implementing integrated e-discovery and compliance platforms?
Common challenges include data migration complexity, user adoption resistance, integration difficulties with existing systems, and the need for specialized training. Organizations should plan for 6-12 month implementation timelines, comprehensive change management programs, and ongoing optimization efforts. Success requires strong executive sponsorship, cross-functional collaboration, and adequate resource allocation for training and support.
Q6: How do modern platforms handle the growing volume and variety of data sources?
Advanced GRC platforms use API-based integration to connect with diverse data sources including cloud applications, collaboration platforms, and mobile devices. They employ AI and machine learning for automated data classification, deduplication, and early case assessment to manage volume efficiently. Platforms also provide scalable cloud architectures that can process terabytes of data without performance degradation.
